Access Control Systems
Our Access Control Systems provide the most extensive line of powerful and versatile Solutions in the industry. As technology continues to evolve and the demands of business professionals worldwide change, Access Control Solutions represent a new revolutionary: Credentials, Topologies and Scalable technologies. The Readers, Controllers, Standard & Enterprise Level Software and accessories are of international & world wide industry standards. They are designed to meet the demands of open architecture, IP-centric environments which provides fully distributed intelligence and decision making right to the door, leveraging the IT infrastructure to the maximum extent possible.
Our Solutions Consist of:-
Identification Credentials/Readers like-Proximity, Smart card, Finger scan, Palm scan, Face recognition, Iris scan, QR Code and Multi-readers.
Topologies comes with various Technologies Like: Wired & Wireless (Virtual network/WiFi online sol./Bluetooth low energy and NFC-near field communication)
Scalability to expand the Access Control System from single door controller to multi door controller, from one location to multi location solutions and Standard Enterprise Level Software.
Identification Credentials:-
RFID Proximity/Smart Card & Multi Identification Technologies

Is the industry’s most extensive selection of reader technologies in today’s security market. We have range from ultra-high frequency, high-frequency, multi-technology or legacy contactless reader technologies (Proximity, Mifare, Flex smart, Desfire , ISO 14443A, ISO 15693 and Felica) to suit the customer’s access control requirements. Access control’s multi-technology solutions enable gradual migration to new standards - reducing impact on resources.
Using RFID Proximity 125 KHz or Smart card 13.56 MHz gives the highest level of security and convenience to access control solutions. Multiple credential technologies supports a wide range of form factors including cards, fobs, wristbands and mobile devices.
These readers has been comprehensively sealed against invasive moisture, dust and liquid. Featuring IP65-rated protection, meticulous sealing, and extra protective engineering, it is ensured that they will operate with unmatched reliability in all type of installation environments.
Applications of these readers are: Standalone Access Control for Small Offices, Networked Security for IBS Buildings, Financial and Research Institutes, Time & Attendance for Offices and Factories and for parking management.
Finger/Palm/Face & Iris Technologies

Finger Scan, Face recognition, Palm scan and Iris scan are World’s-Renowned, Powerful, yet sophisticated technologies, making it a truly secure access control system. With unheralded speed and accuracy, the algorithm used, has been proven as the world’s best biometrics algorithm. It exquisitely blends the benefits of a next generation distributed IP system with the high-level security provided by biometrics. We offers the full benefits of a biometric system with a wide range of RF support for multiple authentication modes.
Our Biometrics are the most advanced terminal providing loads of the world’s best features. Powered by latest innovation, to offers unrivalled matching speed, accuracy and level of security.
Packed in an ergonomically-designed structure, provides exceptional performance and usability for diverse access control and time attendance sites, large or small. It has massive memory capacity to manage largest number of users in its class. A single unit of Biometrics can accommodate up to 100,000 users/templates, 500,000 users logs and 5,000,000 text logs.
Our Biometrics allows uninterrupted recognition regardless of all possible indoor lighting conditions as well as outdoor installations. Our products are Rugged IP54 Dust & Waterproof Structure and has been comprehensively sealed against invasive moisture, dust and liquid. Featuring superb IP54 rated protection through meticulous sealing, combined with extra protective engineering, ensures faultless operation even under harsh conditions.
Smartphone/Paper QR Code Technologies

Allows any access control system to use Smartphone as access credentials. The platform consists of a cloud based service, readers and apps. Apps can receive and contain multiple virtual identity credentials. These credentials are presented to QR code readers using NFC, Bluetooth Low Energy or QR. QR reader are capable of reading the codes displayed on a Smartphones, as well as paper. They are Armed with Newland’s fifth-generation of UIMG technology.
Our Embeddable module, Desktop models and PDA QR code scanner have dimensional code scanning platform which can quickly read the one-dimensional or two-dimensional code of Screen and Paper.
They have exceptional motion tolerance of 2.5m/s and large FOV 46°, enhances user experience. It has an IP50-rated seal, renders the scanner impervious to dust, water and other contaminant. It withstands multiple 1.2m drops to concrete (for six sides, one drop per side). The IR sensor in the scanner enables speedy capture of codes presented to it, markedly increasing throughput and productivity.
The application of this system are in building access control, parking management systems and even event ticketing/management systems.
Wired Topologies:-
Wired Access Control Topology

Access control decisions are made by comparing the credential to an access control Panel. This look-up can be done by a host or server, with an access control panel . The development of access control systems has seen a steady push of the look-up out from a central host to the edge of the system, or the reader. The communication will be done through a serial connection RS-485, Wiegand and TCP/IP protocol.
RS 485 communication medium allows long cable to runs, up to 4000 feet (1200 m), where as Wiegand Communication works under 50 mtrs of length and TCP/IP communication medium is robust and gives us more possibilities and flexibility to maintain and run the system smoothly.
Wireless Topologies:-
Wireless Access Control Topology:
Wireless access control platform is designed to give end users ultimate freedom of choice regarding system layout, type and number of access points as well as level of security. In addition to this, our solutions are easily adapts to changing requirements and can deliver scalability no matter what the project size.
Having broadest product portfolios in access control we can fulfill virtually every technical and functional requirement.
Finally, scalability also means downward compatibility as well as upgradability. Our access control systems are designed for long life ensuring end users remain confident that as new versions of management software are released their hardware will continue to be compatible and work with it.
Our Access Control Wireless Network technologies are
- Virtual Network,
- WiFi,
- Bluetooth and
- NFC (near field communication devices).
Wireless Virtual Network
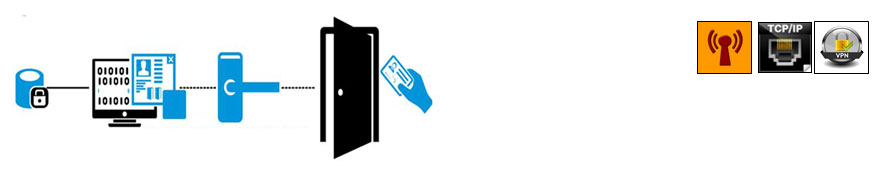
The Virtual Network provides the flexibility for an access control system to grow from a small number of doors and users to a large number of doors and users as required. It allows stand-alone locks to read, receive and write information via an encrypted and secure data-on-card system that utilizes the capabilities of RFID read/write technology.
Wireless WiFi Online Solution
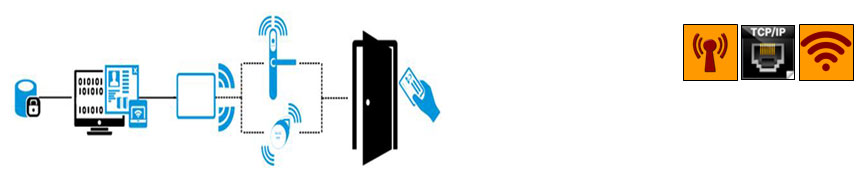
To further the level of security, we have WiFi online solution. It is designed for applications that need high level real-time access control. WiFi uses low power radio transceivers (2.4 GHz). They interact with gateways, which are connected by WiFi to the central management computer. With a single click of a mouse you can configure or make changes to the network in real-time. You can also download audit trail information for real-time control, delete users remotely and securely, collect battery status for maintenance and much more, all from a single PC and all in real-time.
Wireless Bluetooth Low Energy
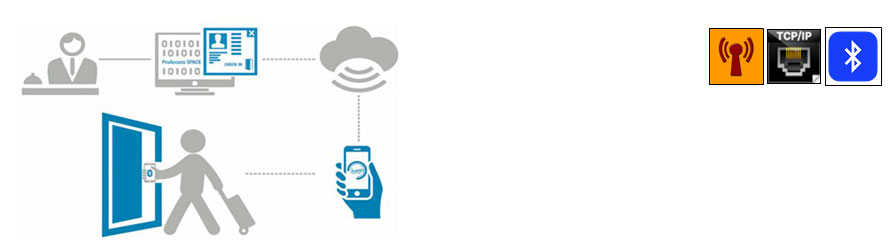
Mobile employs Bluetooth Low Energy (BLE) for communicating between the Smartphone and electronic locks or readers. The mobile key is sent Over the Air (OTA) from the Pro-Access management software to an installed Mobile app at a registered and verified Smartphone. The user receives a message that he has a new key and for which doors he has access rights. Then, they only need to present the Smartphone to the lock and start communication via the Mobile app. All data transmission and the mobile key itself are encrypted and secured against cloning.
Users can receive mobile keys anytime and anywhere. By this, access control solutions gain even more flexibility for issuing and receiving access rights, without sacrificing security.
Wireless NFC (Near Filed Communication)
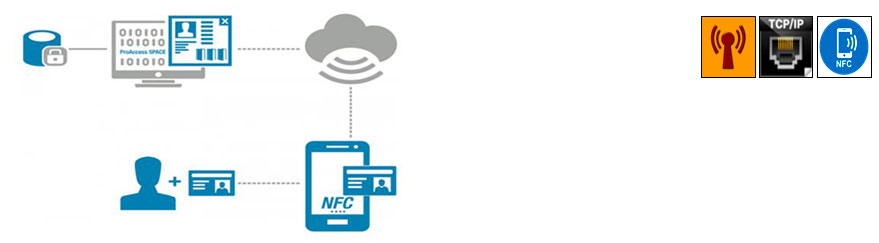
NFC (Near Field Communications) technology developed for getting access and updating access rights to mobile. NFC is the interface for Smartphone. By these means, the possibilities can be expanded to locations where no online wall reader is available. The access rights can be updated via direct communication between the Smartphone and the credential exactly where and when these are needed.
New access rights and black list information are sent to authorized and registered users from app. The NFC-enabled Smartphone then serves as an update point for credentials that an online reader usually does. The end-user updates the credential by presenting it to the Smartphone using the app.
All data transfer is encrypted and secured using Mifare DESFire EV1 technology.
As technology continues to evolve and the demands of business professionals worldwide change, Networked Access Solutions, represent a new revolution in IP-enabled access control solutions. Designed to meet the demands of open architecture, IP-centric environments, provides fully distributed intelligence and decision making right to the door, leveraging the IT infrastructure to the maximum extent possible.
Our solutions easily integrate into existing infrastructure and scale to meet changing needs.
For improved security, reduced costs and more effective response we need to deliver sophisticated Integrated Access Control solutions from the simplest to the most challenging installations.
To protect people and property, we will expand on value added services to meet the needs.
for Enquiry Or |
 StarAxiom Electronics Pvt Ltd
StarAxiom Electronics Pvt Ltd
